Email Deliverability for Crypto Outreach: SPF DKIM DMARC

Cold outreach in Web3 is scam-sensitive, and mailbox providers treat unauthenticated domains as higher risk. When SPF, DKIM, or DMARC are missing or misconfigured, your messages can land in spam, fail to deliver, or trigger trust concerns from founders and operators.
Note: This guide is for agencies and service providers selling services to token-based crypto projects. It is not a guide for token issuers looking for investors or token buyers.
Inside you will learn what SPF, DKIM, and DMARC do, how to set them up, how to test them in a few minutes, and which misconfigurations break inbox placement most often. For a full cold email protocol that includes deliverability guardrails, copy, and sequences, see the step-by-step cold email guide. For compliance and legal framing when buying or using lead data, read the practical guide to crypto B2B leads and compliance.
Who this is for
This article is a technical setup guide for outbound teams that email token-based crypto projects.
- Agencies running cold outreach or lifecycle nurture to sell services.
- Service providers and consultants emailing founders, growth, BD, or ops roles.
- Teams that need repeatable deliverability checks before scaling send volume.
Why deliverability is harder in crypto
Crypto inboxes are filtered more aggressively than many industries, because recipients are trained to expect impersonation, phishing, and hype-heavy spam. That means your technical signals (authentication and domain reputation) and your trust signals (clear identity and non-hype copy) both matter.
What not to promise in Web3 outreach
If your email sounds like a scam, the best DNS setup in the world cannot save it. Avoid promises and patterns that routinely trigger skepticism and filtering in crypto:
- Guaranteed outcomes (for example, "guaranteed growth" or "guaranteed listings").
- Financial upside language (for example, "ROI in 7 days" or "double your token price").
- Pressure tactics (for example, "act now" or "last chance today").
- Vague "partnership" claims (for example, "we have whales ready" or "we can bring investors").
- Unverifiable authority (for example, fake press logos, fake client names, or anonymous sender identities).
A safer baseline is simple, specific service positioning, real proof you can show on a call, and a low-friction question that earns a reply.
SPF setup
SPF (Sender Policy Framework) tells mailbox providers which servers are allowed to send email on behalf of your domain. When a message arrives, the receiving server checks the sending IP against your SPF record in DNS.
What SPF does
SPF answers one question, "Is this sender allowed to send for this domain?" It does not encrypt your message and it does not prove the content was not modified.
How to set up SPF
- Inventory every system that sends email as your domain (mailbox provider, newsletter tool, transactional sender, outreach tool).
- Create one SPF TXT record at the root of your domain that starts with
v=spf1. - Add authorized sources using mechanisms like
include:(provider-supplied) orip4:/ip6:(fixed IPs). - End with a policy qualifier such as
~all(soft fail) or-all(hard fail) once you are confident you listed every real sender. - Publish the TXT record in DNS, then wait for DNS propagation.
Example SPF record (your provider values will differ):
v=spf1 include:sendgrid.net include:mailgun.org ~all
How to test SPF
- Send a test email from your domain to an inbox you control.
- Open the message headers in the receiving inbox and look for an SPF result like PASS or FAIL.
- Fix mismatches by updating the SPF record to include the sender you actually used.
DKIM setup
DKIM (DomainKeys Identified Mail) adds a cryptographic signature to each email you send. The signature lets the receiver verify that the message was sent by an authorized system and that it was not altered in transit.
What DKIM does
DKIM verifies message integrity and domain association via a signed header. It is especially helpful when forwarding breaks SPF, because DKIM can still pass even if the sending IP changes.
How to set up DKIM
- Generate DKIM keys in your email sending provider (mailbox provider or ESP).
- Publish the provided public key as a DNS TXT record, usually under a selector like
selector._domainkey.yourdomain.com. - Enable DKIM signing inside the sending provider, so outbound mail is actually signed.
- Confirm that new messages show DKIM=PASS in headers.
DMARC setup
DMARC (Domain-based Message Authentication, Reporting, and Conformance) tells receivers how to handle mail that fails SPF and DKIM. It also provides reporting so you can see who is sending on behalf of your domain.
How DMARC works in plain English
DMARC checks whether SPF and or DKIM pass and whether they align with the domain in the visible From address. If alignment fails, your DMARC policy tells the mailbox provider what to do next.
How to set up DMARC safely
- Start with monitoring using
p=none, so you can collect reports without impacting delivery. - Review reports to confirm all legitimate sources authenticate and align.
- Tighten policy gradually to
p=quarantine, thenp=rejectwhen you are confident. - Add alignment settings like
aspf=sandadkim=sonly after testing, because strict alignment can break legitimate flows if you are not ready.
Example starter DMARC record (addresses are examples):
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com
Common misconfigurations and fixes
Duplicate SPF records
Symptom: SPF results show PERMERROR or inconsistent fails across receivers. Fix: Keep exactly one SPF TXT record for the root domain, and merge all includes into that single record.
SPF DNS lookup limit exceeded
Symptom: SPF randomly fails even though you listed providers. Fix: Reduce nested includes so you stay under the SPF 10-lookup limit, or remove unused senders.
DKIM selector mismatch
Symptom: DKIM fails because the receiver cannot find your public key. Fix: Confirm the selector name in DNS matches what your sending provider uses, including the full record name.
DKIM record exists but messages are not signed
Symptom: Your DNS looks correct, but DKIM=NONE or DKIM=FAIL appears in headers. Fix: Enable DKIM signing in the sending provider, then retest with a fresh message.
DMARC is too strict too early
Symptom: Legitimate emails are quarantined or rejected after you set DMARC.
Fix: Roll back to p=none, fix SPF and DKIM alignment issues, then tighten policy step by step.
Deliverability pre-flight checklist
Use this checklist before you increase send volume or switch tools.
- Confirm you control the From domain you are sending as.
- Verify SPF has one record only, and it covers every legitimate sender.
- Check DKIM is enabled and signing for every sending system.
- Add DMARC with
p=nonebefore moving to quarantine or reject. - Ensure the From domain aligns with DKIM and or SPF where possible.
- Validate reply-to addresses and mailbox ownership for every sender identity.
- Keep list quality high; validate your list before scaling using a repeatable hygiene workflow, because bounces damage reputation faster in crypto outreach.
- Rate limit early sending, and avoid sudden volume spikes.
- Include a clear opt-out path and honor suppression lists consistently.
- Retest after any DNS change, new inbox, new tool, or new sending subdomain.
For landing pages and web workloads, keep them on separate infrastructure from email sending; how to choose low-cost VPS for outreach ops walks through options. If you send via EmailOctopus for newsletters or nurture, EmailOctopus deliverability for crypto outreach covers setup and warm-up.
Testing checklist
The fastest way to validate SPF, DKIM, and DMARC is to send a real message and inspect the authentication results.
- Open the sending mailbox you want to test.
- Compose a simple message with a neutral subject and plain text body.
- Send it to a different inbox you control.
- Locate the received message, then open the header view.
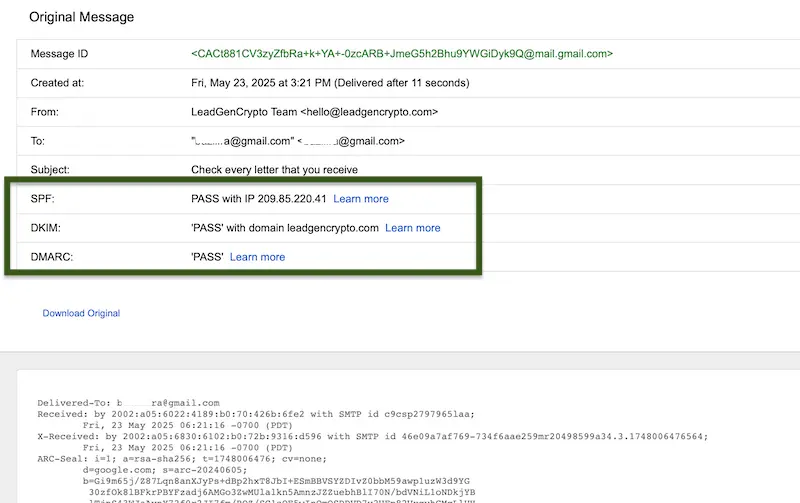
- Look for SPF, DKIM, and DMARC results, and confirm they show PASS.
The example below shows how to do this in Gmail using "Show original."
A correctly authenticated message shows PASS for all three checks.
For deeper diagnostics, run a full deliverability report before scaling, using this walkthrough: Test deliverability with Mail-Tester.
If you want a small, real-world test list to validate inbox placement safely, start here: Get a free lead.
Warm-up and sending ramp
New domains and new inboxes need a conservative ramp, even when your DNS is perfect. Warm-up is not a license to spam, it is a way to build a clean sending history while you keep targeting tight.
A simple next step is to follow a structured warm-up plan and pause when you see warning signs: Email warm-up for crypto outreach.
Copy-level risk words
Authentication gets you verified, copy gets you believed. If your message reads like hype or pressure, crypto recipients will ignore it and filters may learn to distrust it.
For practical rewrites and safer alternatives, use this guide: Crypto outreach spam words and safer alternatives.
Where LeadGenCrypto fits
Deliverability is not only DNS, list quality also matters.
Verified contacts help reduce bounce risk, which protects your sender reputation while you run outreach tests. Exceptions and suppression hygiene reduce duplicates, repeat touches, and complaint risk over time.
To keep your outreach cleaner as you scale, review this setup: Filters and Exceptions.
LeadGenCrypto • Blog & Newsletter
Deliverability tips and sales playbooks, in your inbox
Subscribe for timely updates, practical sales advice, and useful resources for teams selling services to crypto projects. Straight to your inbox, easy to skim.
- Quick summaries of our latest articles so you stay current without the reading pile
- Actionable ideas to boost sales, from deliverability to sequences and closing
- Templates, checklists, and benchmarks you can use with your team this week
- No hype. Unsubscribe anytime with one click.
